In today’s dynamic digital landscape, where the pace of software development is accelerating at an unprecedented rate, the need for a robust and secure DevOps pipeline has never been more critical. DevOps, the amalgamation of development and operations, streamlines the software development lifecycle, empowering teams to deliver applications faster and more efficiently. However, this efficiency comes with its own set of challenges, particularly in terms of cybersecurity.
As organizations increasingly embrace DevOps methodologies, they must prioritize the security of their pipelines to safeguard against cyberattacks that could compromise sensitive data, disrupt operations, and tarnish reputations. This comprehensive guide aims to provide in-depth insights and actionable best practices
DevOps involves continuous integration, continuous delivery (CI/CD), and continuous deployment, allowing teams to iterate and release software updates rapidly. While this agility is a boon for development teams, it also opens up potential vulnerabilities that malicious actors may exploit.
Implementing a Security-First Mindset
The first line of defense in securing your DevOps pipeline is fostering a security-first mindset within your development and operations teams. This involves integrating security practices seamlessly into the entire software development lifecycle, from code creation to deployment.
Training and Awareness: Conduct regular and comprehensive training sessions to educate your teams about the latest cybersecurity threats and best practices. Awareness is the first step towards building a proactive defense against potential attacks. Provide real-world examples and case studies to illustrate the impact of cyber threats on DevOps pipelines.
Collaboration Between Teams: Facilitate robust collaboration between development and operations teams, emphasizing the shared responsibility for security. Establish clear communication channels and encourage cross-functional teams to ensure that security considerations are integrated at every stage of the pipeline. Highlight successful case studies where collaborative security efforts led to a strengthened DevOps ecosystem.
Ensuring Code Quality with Automated Testing
Automated testing is a cornerstone of DevOps, ensuring that code changes do not introduce vulnerabilities or compromise the integrity of the application. By integrating security testing into your automated testing processes, you can identify and address potential issues early in the development cycle.
Static Application Security Testing (SAST): Delve deeper into the implementation of SAST tools to analyze the source code for security vulnerabilities. Explain how these tools identify potential weaknesses in the codebase, such as injection flaws or insecure dependencies. Provide a step-by-step guide on integrating SAST into the development workflow, emphasizing its role in preventing common security pitfalls.
Dynamic Application Security Testing (DAST): Explore the nuances of DAST tools and their role in conducting dynamic testing in runtime environments. Highlight how DAST tools simulate real-world cyber threats, uncovering vulnerabilities that may not be apparent in static analysis. Provide practical examples of how DAST can complement SAST to offer a more comprehensive security assessment.
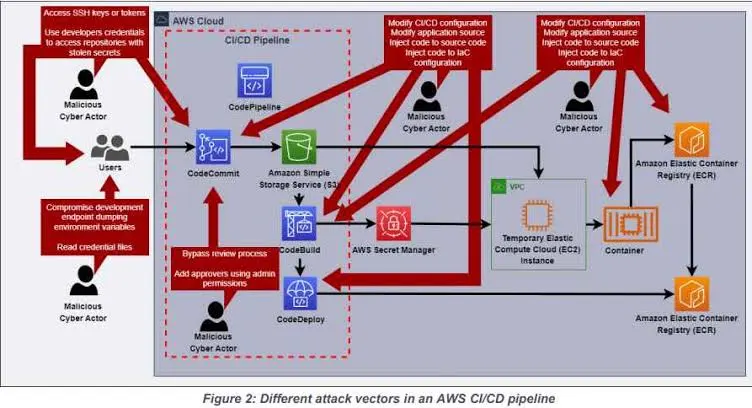
Securing the CI/CD Pipeline
The continuous integration and continuous delivery pipeline is the heartbeat of DevOps, automating the process of building, testing, and deploying code changes. Securing this pipeline is paramount to prevent attackers from injecting malicious code or compromising the integrity of the software.
Access Control and Authentication: Dive deeper into the implementation of strict access controls to limit who can make changes to the CI/CD pipeline. Elaborate on the use of multi-factor authentication to enhance security and ensure that only authorized personnel can initiate deployments. Provide case studies illustrating the consequences of unauthorized access and emphasize the importance of stringent authentication measures.
Code Signing: Explore the intricacies of code signing mechanisms and their role in verifying the authenticity and integrity of code before deployment. Explain how code signing ensures that only authorized and unaltered code is pushed into production, reducing the risk of malicious injections. Provide step-by-step guidelines on implementing code signing in the CI/CD pipeline.
Contaier Security Best Practices
Containers have become instrumental in DevOps for their ability to package and isolate applications along with their dependencies. However, without proper security measures, containers can become a vector for cyber threats.
Image Scanning: Delve into the details of regularly scanning container images for vulnerabilities and ensuring that only trusted and secure images are used in the deployment process. Explore automated tools that can identify and flag potential risks, allowing teams to address issues before deployment. Provide real-world examples of security breaches stemming from unsecured container images.
Runtime Security: Explore the nuances of implementing runtime security measures to monitor containerized applications in real-time. Explain how anomaly detection, intrusion prevention, and behavior analysis can identify and mitigate potential threats during runtime. Provide case studies illustrating the effectiveness of runtime security in preventing and responding to container-related security incidents.
Continuous Monitoring and Incident Response
In the dynamic DevOps environment, continuous monitoring is indispensable for detecting and responding to security incidents promptly. Implementing a robust incident response plan ensures that your team can address potential threats efficiently and minimize the impact of a security breach.
Log Analysis and Monitoring: Dive deeper into the best practices of centralizing and analyzing logs from various components of your DevOps pipeline. Explain how monitoring for unusual patterns or suspicious activities can help identify potential security incidents before they escalate. Provide insights into the tools and technologies that facilitate effective log analysis and monitoring.
Automated Incident Response: Explore the intricacies of leveraging automation to streamline the incident response process. Explain how automated responses can isolate compromised components, roll back changes, and trigger alerts for manual intervention, reducing the time it takes to mitigate the impact of a security incident. Provide practical examples of how automated incident response measures have proven effective in real-world scenarios.
Conclusion
Securing your DevOps pipeline from cyberattacks is an ongoing process that demands a nuanced understanding of the DevOps landscape and a multifaceted approach to security. By adopting a security-first mindset, implementing automated testing, securing the CI/CD pipeline, prioritizing container security, and establishing continuous monitoring and incident response capabilities, you can fortify your digital fortress and navigate the evolving landscape of cybersecurity threats.
As the DevOps landscape continues to evolve, staying informed about emerging threats and adopting innovative security solutions will be key to maintaining a resilient and secure DevOps pipeline. By investing in security measures and empowering your teams with the knowledge and tools they need, you can confidently embrace the benefits of DevOps while mitigating the risks associated with cyber threats.